ISO 27001 Information Security Management System

IF YOU AREN’T MANAGING RISKS, YOU SHOULD BE The issue of information security sees organisations of all sizes and from all sectors, with an identical problem – their inherent vulnerability.
No matter how secure and well protected an organisation appears to be, sensitive information can be leaked without you even realizing until it’s too late. All information in all departments, whether on computer disk, paper or in the heads of those you employ, is at risk from any number of very real threats. Information security is no longer just an issue for IT managers – a single breach of information security could cost your company hard earned profits whilst doing irreparable damage to your image and reputation. Your capacity to trade profitably depends on your ability to manage this risk effectively.
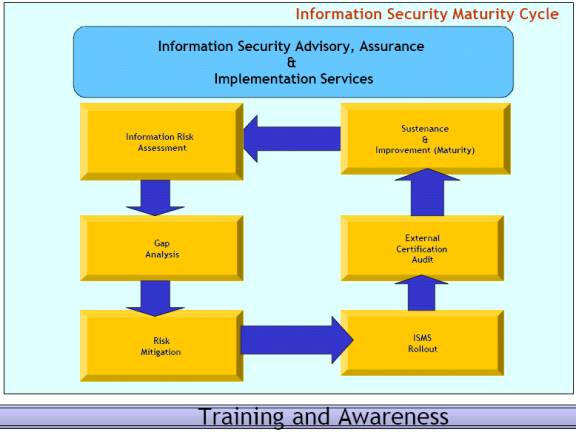
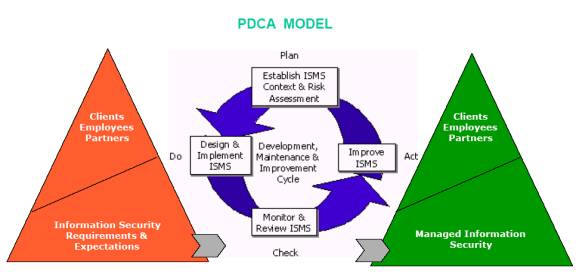
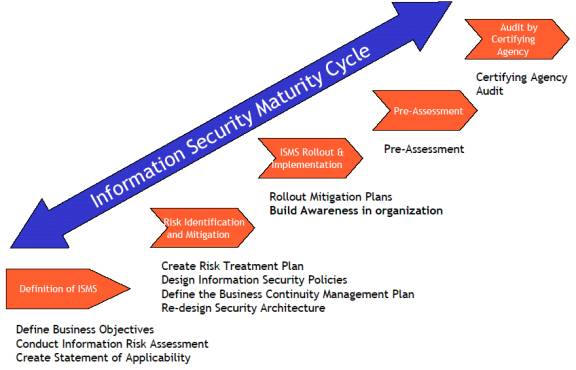
As the number of reported information security breaches consistently increases, the need to create a management framework for information security intensifies. An Information Security Management System (ISMS) – ISO 27001:2013. Once you start using ISO 27001 as a basis for your ISMS, your management system can be audited and registered by a third party. This process adds significant value to the ongoing effectiveness of the system.
An enabling mechanism An enabling mechanism whose application ensures that information may be shared shared in a manner that ensures the appropriate protection of the information & associated information assets
– Build on a Common Basis for Organisational Security Standards Development
– Enhance Security Management Practice
– Increase Confidence and Trust in Inter-Organisational Dealings


Features & Benefits
Security policy
A document to demonstrate management support and commitment to the Information Security Management System process.
Security organisation
An established management framework to initiate and control the implementation of information security within your organisation and to manage ongoing information security provision.
Asset classification and control
A comprehensive inventory of assets with responsibility assigned to ensure that effective security protection is maintained.
Personnel security
Well defined job descriptions for all staff outlining security roles and responsibilities.
Physical and environmental security
A clear and concise definition of the security requirements for your premises and the people within them.
Communications and operations management
Optimise your communication to facilitate smooth operation of the Information Security Management System.
Access control
Network management to ensure that only those with the appropriate responsibility have access to information in the networks and the protection of the supporting infrastructure.
Systems development and maintenance
Ensuring that IT projects and support activities are conducted in a secure manner through data control and encryption where necessary.
Business continuity management
A managed process for developing and maintaining business contingency plans, which protect critical business, processes from major disasters or failures.
Compliance
A demonstration to clients, employees, and the authorities of your commitment to meet statutory or regulatory information security requirements.
